Blog
Oct 15, 2020
A Path to Success in the PWK Labs
As part of our ongoing efforts to support student success, we’re introducing a new learning path for the PWK labs. Find out more – along with pass rate data.
4 min read

Our goal has always been to empower our students to succeed and progress professionally. We have spent some time thinking about how else we can assist PWK students on their journeys, and have created a learning path that should provide students with a starting point for the PWK labs, making the network more approachable.
Since the inception of Penetration Testing with Kali Linux (PWK) and Penetration Testing with BackTrack (PWB) before that, one of the hallmarks of OffSec’s pentesting training has been our extensive course labs. The idea was simple: create a lab environment in which our students could directly apply the techniques learned from the course book, and do so in a way that simulates a real network.
The deliberate coupling of the course materials with our unique PWK labs make the networks we have created a core part of the curriculum and the learning experience. In our own professional careers, we have repeatedly used penetration testing methodologies and approaches that tend to manifest themselves in a cyclical manner. The techniques and attacks we used produced results that became the building blocks towards a better understanding of an interconnected organizational network.
While there is no doubt that CTF-style, one-off targets can be a valuable learning tool for particular techniques, they fail to capture an important aspect of penetration testing, namely the complexity of a real-world network. This is what our PWK labs are designed to simulate.
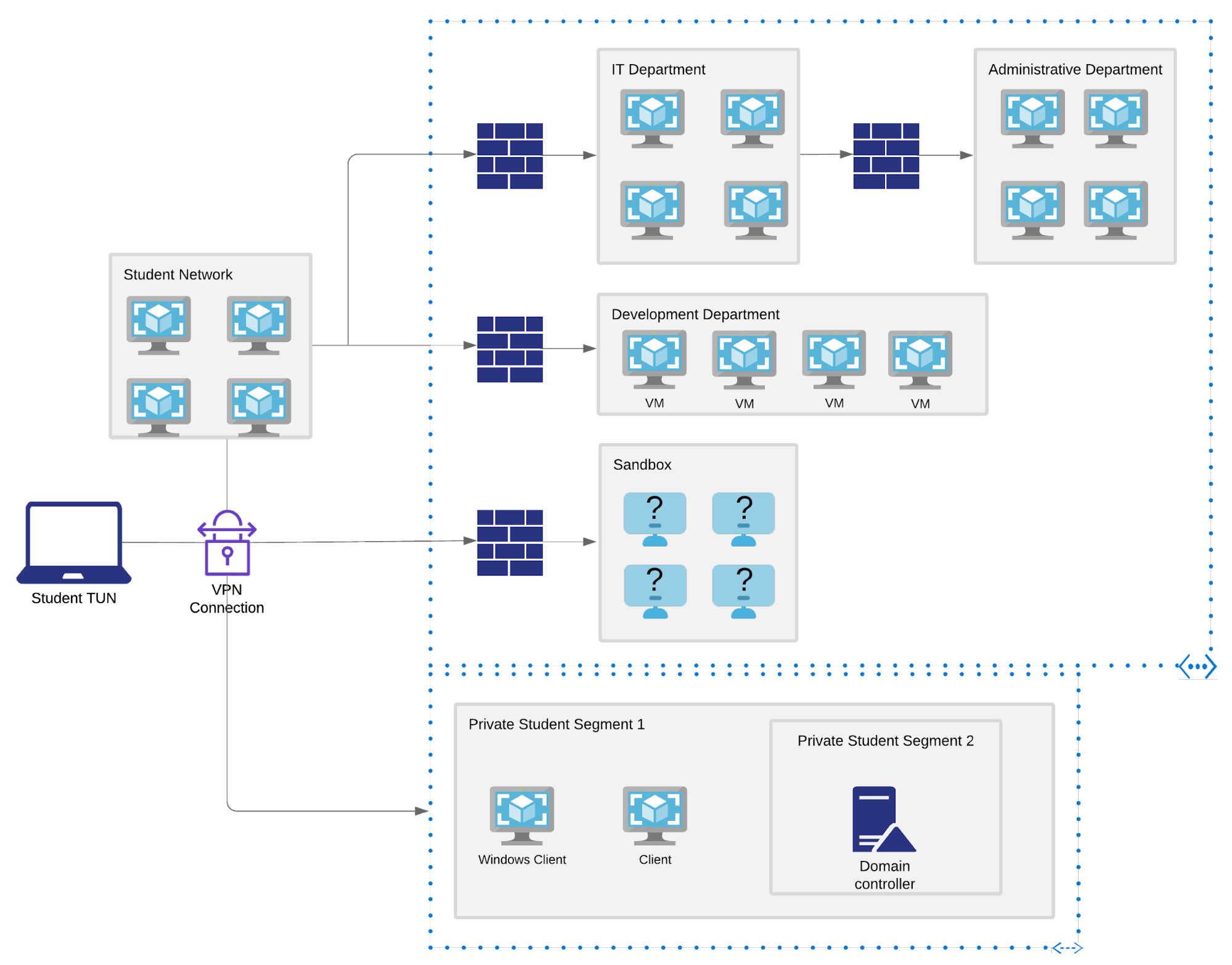
This design has always included machine dependencies, credential reuse, hard-to-reach subnets, tunneling, and various other network characteristics that security consultants face on a regular basis. In our most recent PWK update, we also introduced small Active Directory deployments in the labs which are designed to reinforce newly added course material.
Over the course of its existence, the PWK network has grown substantially. It currently includes over 70 machines, four subnets with dependencies (including double pivoting in place since 2008), and three Active Directory deployments, including the Sandbox network that was designed to be a case study for a small, example security assessment.
As a consequence, the PWK labs are rather complex.
Depending on the prior experience of a PWK student, this complexity can be daunting. While we have always been strong believers in a lightly assisted, more hands-on mentored approach to learning, we understand that some students could use more lab guidance in order to get the most out of their PWK learning experience. This notion is supported by student feedback, as well as our own statistical analysis.
A Quick Look at PWK Statistics
Although we have rarely released any data related to success and failure rates of OSCP exam takers, we have always maintained a close eye on developing trends within our courses, labs and exams. One of the most obvious and important metrics for student success is the OSCP pass rate.
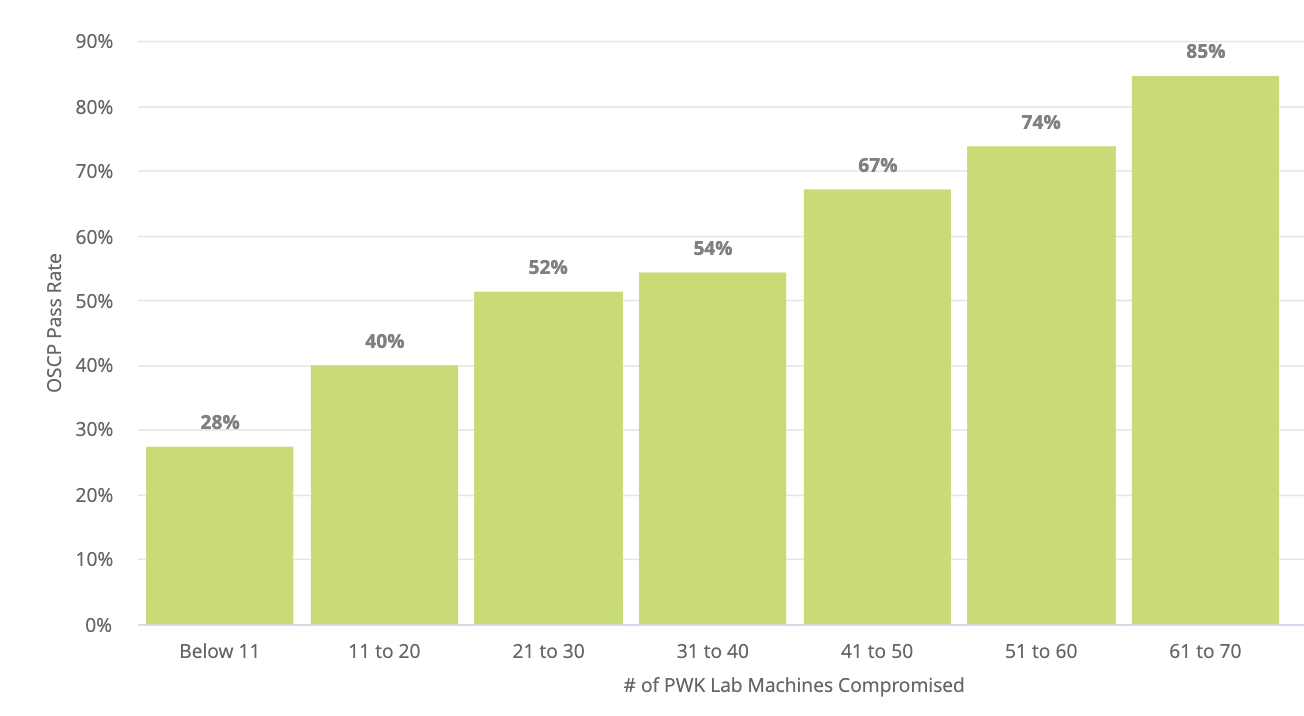
Analysis of our data shows a strong correlation between the number of machines compromised in the PWK labs and the OSCP pass rate. The following chart includes the data since the PWK 2020 update and provides a high-level overview of that correlation.
It is important to note that the number of exploited machines alone is not a good estimation of success. How the student exploited those machines and what they learned in the process is far more important. In other words, simply following a walkthrough for any given machine is not a substitute for actual learning.
This certainly doesn’t come as a surprise as there are no shortcuts to learning. The more time a student spends practicing PWK materials and techniques in the labs, the higher their chances of passing the OSCP exam.
Intro to the PWK Labs Learning Path
So what is the PWK labs learning path? In a nutshell, it is a collection of PWK lab machines for which we are issuing more detailed and public guidance. When followed, this guidance should provide students with an enhanced learning experience. Additionally, we are mapping these machines directly to the relevant modules in the PWK course book, so that students can relate certain techniques to specific machines in the labs.
Detailed information about the learning path machines can be found on our Support Pages.
While it is important to describe what the learning path is, it is equally important to clearly state what it is not.
- It is not a complete map of the entire network with solutions.
- It is not a complete mapping of course modules to specific machines in the labs.
- It is not a subset of machines that guarantees passing the OSCP exam.
We hope that the addition of the more detailed guidance will provide our PWK students with more tools to have a productive and fulfilling learning experience.
Stay in the know: Become an OffSec Insider
Get the latest updates about resources, events & promotions from OffSec!
Latest from OffSec

Research & Tutorials
CVE-2024-13059: Exploiting Path Traversal in AnythingLLM for Remote Code Execution
Discover CVE-2024-13059, a critical vulnerability flat that affects AnythingLLM’s handling of ASCII filenames in the multer library.
Apr 17, 2025
2 min read

Enterprise Security
How OSCP Holders Can Lead Their Teams to Greater Cybersecurity Resilience
Champion OSCP training in your organization to build a unified, resilient security team.
Apr 11, 2025
6 min read

Research & Tutorials
CVE-2024-57727: Path Traversal Vulnerability in SimpleHelp Web Application
CVE-2024-57727 lets attackers read sensitive files via path traversal in SimpleHelp. Learn more about how attackers exploit this flaw.
Apr 10, 2025
3 min read