Blog
Nov 10, 2022
Exploit Database 2022 Update
We’re sharing some significant updates to Exploit Database, one of OffSec’s community projects.
2 min read

It’s been a minute since we last talked about Exploit Database, one of our community projects. Today we are excited to announce new updates!
Here are the highlights of this Exploit-DB update:
-
- We added a few fields into the database dump, including CVEs
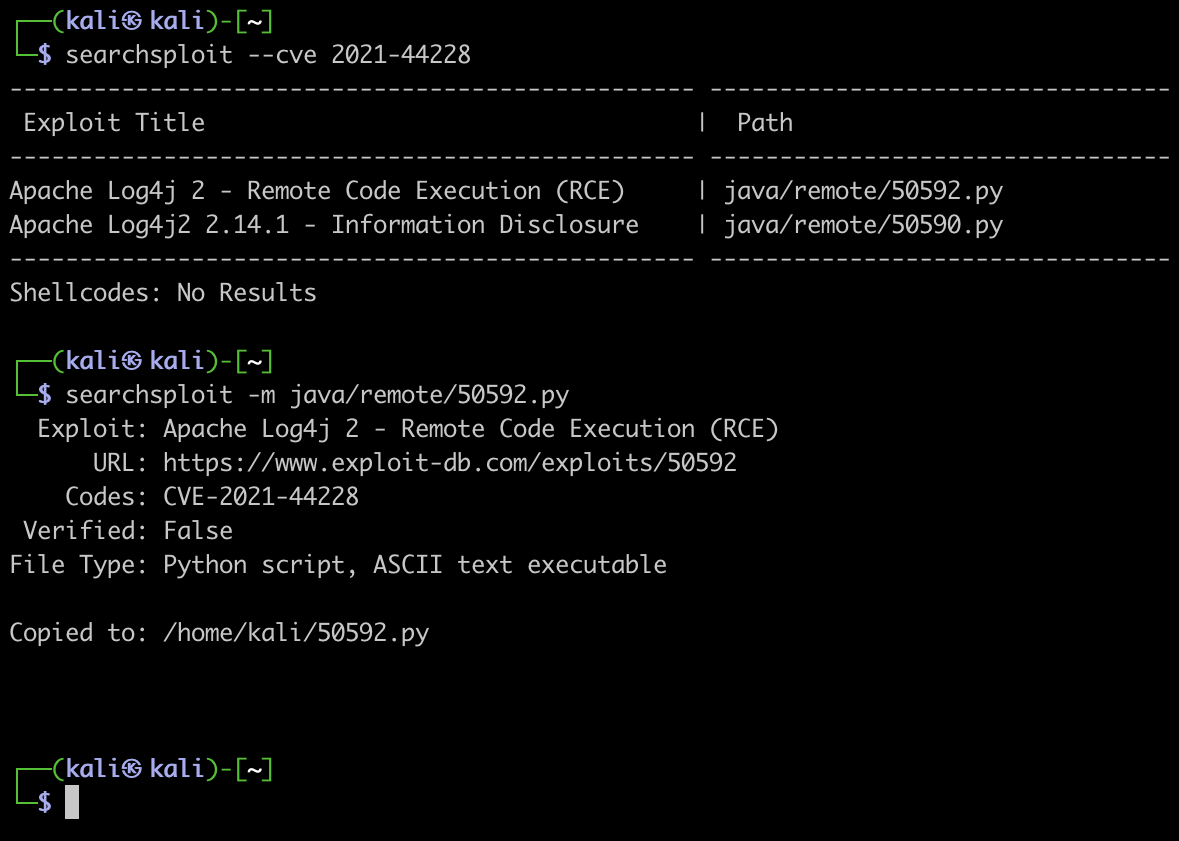
- SearchSploit has also been updated to allow for searching (
--cve)
- SearchSploit has also been updated to allow for searching (
- We are now distributing Google Hacking Database (GHDB)’s database dump
- Asking for help with this from the community
- We have moved from GitHub to GitLab
- Roadmap Plans
- We added a few fields into the database dump, including CVEs
Exploit-DB Full Dump
Previously, when we were distributing the database dump, the main “content” of each exploit and the “metadata” was reserved for “EDB Partners.”
However, as of today, this is changing. We are giving everything away!
The extra values included are:
-
- Aliases – Other names of identifying the item
- Application URL – A link to the mirror of the setup file
- CVE – A method of identifying vulnerabilities
- Date Added – When was it added to EDB (rather than when the code was created)
- Date Updated – When was it last updated on EDB
- Screenshot URL – A link to our screenshot as proof
- Source URL – Where the code came from (aka upstream)
- Tags – Grouping items together
- Verified – Has the EDB team confirmed the exploit works?
CVEs
This update includes the highly requested “Common Vulnerabilities and Exposures (CVE)” values for exploits. A “CVE” is a way of identifying vulnerabilities and has become the “industry standard” – for better or worse, but that’s a conversation for another day.
We have also updated SearchSploit to allow for searching for CVEs:
Google Hacking Database (GHDB) Full Dump
We are now also sharing the GHDB database with you! Currently, it is in a different format (XML rather than CSV & TXT), but like EDB, it should be a complete dump.
We have yet to generate a tool like SearchSploit to handle GHDB, so we are calling the community to develop the official tool! The tool can either be another stand-alone or extend SearchSploit functionally. If if you are up for the challenge, then please open up a merge request.
New Home
Previously, we were on GitHub. However, Exploit-DB is now completely moved to GitLab. Kali Linux did it a while ago, and we’re following suit.
Future Plans
For 2023, we are hoping to introduce more new features. We often see people opening up pull/merge requests to either update or add code. However, we are dumping our database. Thus it is one direction only. We are working on a system to become bi-directional, allowing for edits to happen via Git.
Furthermore, we’re looking at refreshing Google Hacking Database to be more of a “dork database,” so the naming allows for more excellent coverage of other services.
Until the next update – happy sploit’ing!
Stay in the know: Become an OffSec Insider
Get the latest updates about resources, events & promotions from OffSec!
Latest from OffSec

Research & Tutorials
CVE-2024-13059: Exploiting Path Traversal in AnythingLLM for Remote Code Execution
Discover CVE-2024-13059, a critical vulnerability flat that affects AnythingLLM’s handling of ASCII filenames in the multer library.
Apr 17, 2025
2 min read

Enterprise Security
How OSCP Holders Can Lead Their Teams to Greater Cybersecurity Resilience
Champion OSCP training in your organization to build a unified, resilient security team.
Apr 11, 2025
6 min read

Research & Tutorials
CVE-2024-57727: Path Traversal Vulnerability in SimpleHelp Web Application
CVE-2024-57727 lets attackers read sensitive files via path traversal in SimpleHelp. Learn more about how attackers exploit this flaw.
Apr 10, 2025
3 min read