Information Gathering
a11y.text Information GatheringInformation Gathering with Metasploit
a11y.text Information Gathering with MetasploitThe foundation for any successful penetration test is solid reconnaissance. Failure to perform proper information gathering will have you flailing around at random, attacking machines that are not vulnerable and missing others that are.
We’ll be covering just a few of these information gathering techniques such as:
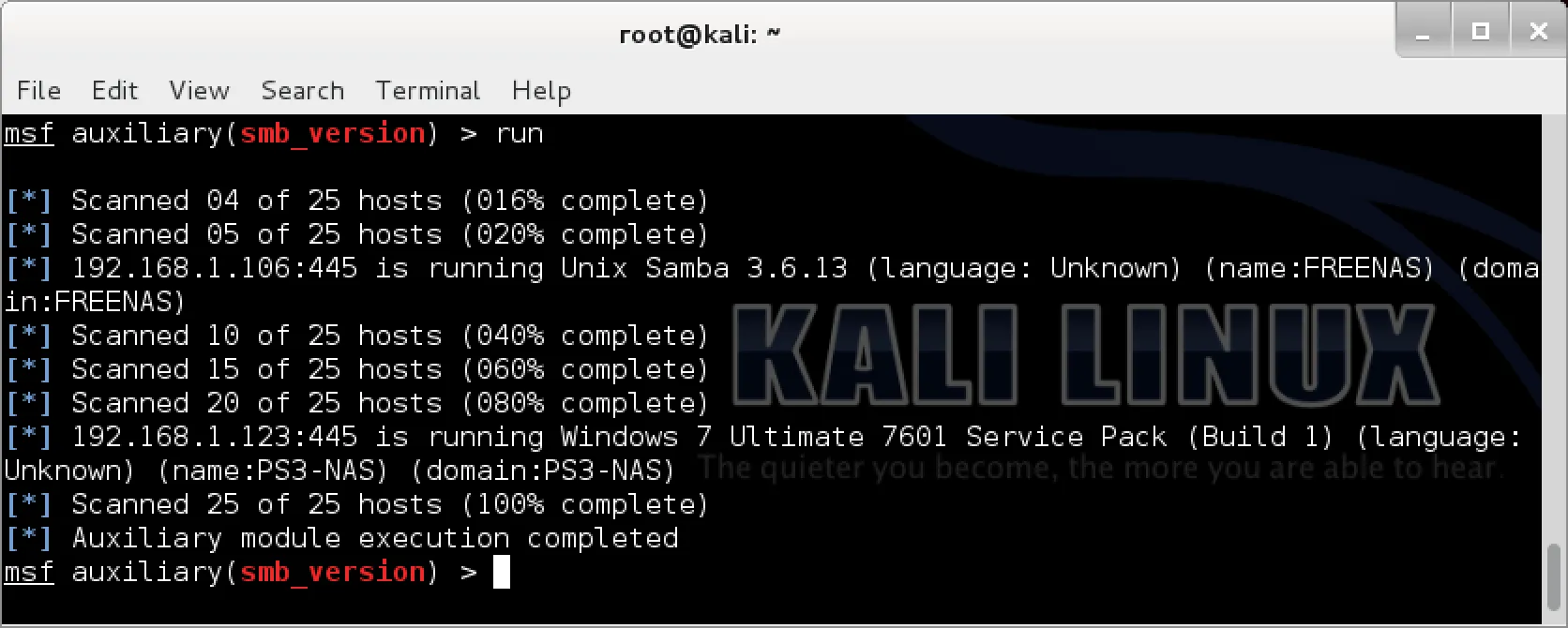
Let’s take a look at some of the built-in Metasploit features that help aid us in information gathering.