Blog
Sep 3, 2013
Penetration Test Report 2013
We are proud to release a new, updated, sample penetration test report. This report accurately reflects the types of assessments we conduct for our clients. It incorporates changes we have made over the last two years based on customer feedback, as well as reflecting many of the types of attacks we have found to be effective in multiple customer environments.
3 min read

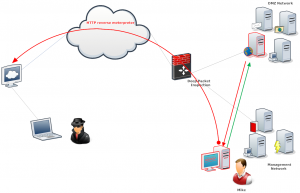
Offsec Pentesting Report Updated
We are proud to release a newly updated sample penetration test report. This report accurately reflects the types of assessments we conduct for our clients, incorporating changes we have made over the last two years based on customer feedback, as well as reflecting many of the types of attacks we have found to be effective in multiple customer environments.
Our last publicly released penetration test sample report generated a lot of discussion on what should, and should not, be in a report. Blogs were inspired by it, universities have used it in classes as part of their courseware, and overall it has become the gold standard that other reports are compared to.
While a lot of that is flattering, there is something important to remember: Our penetration test reports are designed to convey information that is relevant for the type of penetration tests that we conduct. We strive to structure our penetration tests in a manner that accurately simulates the actions of a highly skilled malicious party conducting a targeted attack against your organization.
Many organizations will conduct assessments in support of audit or other compliance efforts. These assessments bring with them their own reporting requirements, which are not reflected in our example, simply because we do not conduct compliance-based assessments. We encourage everyone who wants to use this report as an example for their own work to think critically about what they are trying to communicate and how best to do it. Don’t just blindly copy this format, as the results won’t be what you are looking for.
Often times, our customers are organizations that have been through multiple rounds of assessments and are having trouble finding a vendor that is up to the challenge of a highly secured environment. The attack simulations that we conduct are highly customized to the targeted organization and many involve the discovery and development of 0-day attacks.
Our reporting format is designed with these customers in mind. We strive to provide a clear narrative that demonstrates how controls are bypassed in addition to direct recommendations on how to mitigate or prevent successful attacks. Give it a read, and see if its right for you.
What is a Pen Test?
Interested in learning more about our penetration testing services? We’re more than happy to discuss your pentesting needs. Contact Offsec today!
[/vc_column_text][/vc_column][/vc_row]
Stay in the know: Become an OffSec Insider
Get the latest updates about resources, events & promotions from OffSec!
Latest from OffSec

Enterprise Security
How OSCP Holders Can Lead Their Teams to Greater Cybersecurity Resilience
Champion OSCP training in your organization to build a unified, resilient security team.
Apr 11, 2025
6 min read

Research & Tutorials
CVE-2024-57727: Path Traversal Vulnerability in SimpleHelp Web Application
CVE-2024-57727 lets attackers read sensitive files via path traversal in SimpleHelp. Learn more about how attackers exploit this flaw.
Apr 10, 2025
3 min read

Penetration Testing
AI Penetration Testing: How to Secure LLM Systems
Explore how AI penetration testing enhances LLM security, addressing unique vulnerabilities and improving cyber defenses.
Apr 3, 2025
8 min read