
Mar 24, 2020
Attacking the Web: The Offensive Security Way
OffSec student 0xklaue wrote this review of Advanced Web Attacks and Exploitation and the OSWE exam. Find out how to prepare and what you need to know.
This article originally appeared on Mar 18, 2020, posted by 0xklaue. It has been posted with minor edits, with permission from the author. Original post: https://medium.com/@0xklaue/attacking-the-web-the-offensive-security-way-b38bea609318
My review on AWAE course and corresponding OSWE exam
I personally love The Web Application Hacker’s Handbook, since it is regarded as the Bible of black box web application security testing by many web application security researchers, and bug bounty hunters. The book speaks heavily about finding security issues that lay in a web application without having access to its source code. But some issues are harder to find, not easy to spot, just because they lie deep down as a mystery in the source code. The source code of web application is the one who asks for you to have a deep, closer look till your eyes hurt.
The Advanced Web Attacks and Exploitation, also known as AWAE, is a course provided by Offensive Security which speaks heavily about finding security issues in a web application, and combining security issues with problems in the source code of an application, maximizing the resultant of the security issues until the underlying hosting server squawks back to you, i.e., resulting in a remote code execution. This course was an exclusive course (similar to their Advanced Windows Exploitation course) that was only available in Blackhat. Thankfully, Offensive Security were kind to roll out their AWAE course for everyone. They made a beta release almost a year ago for existing Offensive Security certification holders.
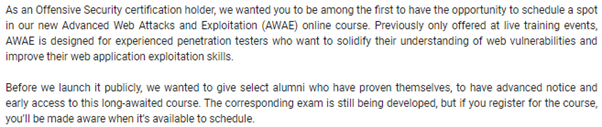
Few days later, they made it public that AWAE course has now been made available for all
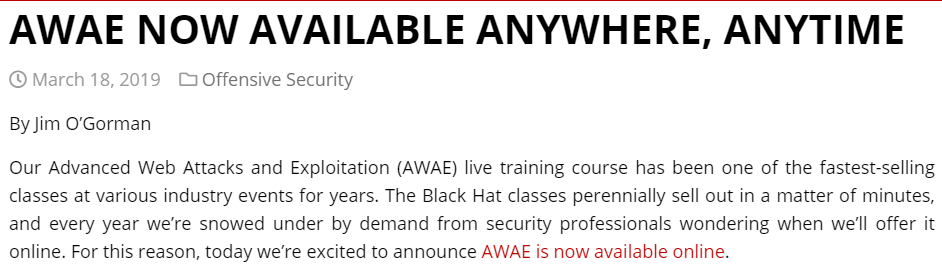
Jim O’ Gorman is by the way right about one thing: This course gets sold out in just minutes at BH events. FYI: Jim is one of the senior folks at OffSec, and one of the co-authors of Metasploit: The Penetration Tester’s Guide.
The course was originally created by mr_me, but the baton has been passed to ronin and ryujin. Offensive Security has published the syllabus of the course, and you would notice right away that you do not stop when you find flaws like XSS, CSRF, and SQL injection, but you are made to work hard till you hit the home run, i.e., remote code execution, simply because (a) It’s Offensive Security, and (b) Why stop at a petty XSS when you can put maximum effort to get an RCE!

So, what do I need for this course?
Excellent question. Many people still wonder what it takes to go toe-to-toe in order to get the best out of this course. I’ve made a list of the following:
- Offensive Security Certified Professional(OSCP) / General understanding of web app attack vectors, theory, and practice – OSCP is not a must have because PWK and AWAE are two separate courses focusing on two separate security platforms, but you should at the least know the basics of HTTP, XSS, CSRF, and other web application attacks.
- Ability to write simple Python / Perl / PHP / Bash scripts – Not simply because its fancy to automate exploitation process, but it saves a lot of your time. You will thank your scripting skills during the course. My recommendation is to learn python because (1) this language has been widely used in the course for scripting (2) I was familiar with python scripting, AND its libraries make it my favourite language.
- Familiarity with Burp Suite – If you have spent a fair share of your time with Burp Suite community edition, you should be fine.
- Notepad++ – Not for viewing code, but for using its searching capabilities
- Regex – If you can figure out what [2–9]|[126]\d|3[0–6] means, then you are good to go. If not, I should suggest you to get familiar with it.
What about tools like, say, SQLMap?
No, this is not an option here.

This course wants you to understand the code flow, the exploitation process, and if the vulnerability requires further research, you should chain the vulnerabilities to get what you desire – such as data exfiltration by leveraging an XSS with implementing a regex bypass.
Offensive security does not promote tools which automate the exploitation process. If you want to know which tools are not allowed specifically, as mentioned in OSWE exam guide, they are:
- Source code analyzers – Such as sonarqube
- Automatic exploitation tools (e.g. db_autopwn, browser_autopwn, SQLmap, SQLninja etc.)
- Mass vulnerability scanners (e.g. Nessus, NeXpose, OpenVAS, Canvas, Core Impact, SAINT, etc.)
- Features in other tools that utilize either forbidden or restricted exam limitations
What do I need in order to prepare?
There are very good resources out there, such as those of wetw0rk, deletehead, timip, which cover almost everything that you would be needing to prepare for AWAE course, but these are few things that are expected from you:
- Understanding different programming languages such as PHP, Java, NodeJS, .NET, JavaScript – You may not be expert in all, which is okay, but please don’t freak out when you see the magnitude of the code base. Follow the supplementary videos of relevant module, do extensive research about the concepts and topics and you would be good to go :-)
- Python – Since you will find a lot of python2 scripts in the courseware, it is expected to have a decent familiarity with the said language. Fair scripting skills are plus.
- Understanding databases such as MySQL and PostgreSQL – Not for DBMS, but for shells. Once you enter the ManageEngine module, your mind will be blown away with the ways you can get a shell.

- Understanding web application vulnerabilities which exist in OWASP Top 10 2017.
- Scripting skills.
- Rectification and automation of exploits.
- Different ways to debug a piece of code, such as simply writing “console.log()” statements to print output in JS.
- Dynamic debugging with dnSpy. dnSpy is a great tool for debugging .NET web applications, even if you do not like it during AWAE course.
- Preparation to read code and do research accordingly! – You will be thrown to multiple languages, which have fairly good amount of lines of code which may seem endless.
- Virtues such as patience, focus and will – Believe me, this course will drain your energy if you plan to go through a module unprepared. If you do, make sure you have patience to sit through and analyse how the code flow occurs, take notes to understand what is going on, recreate the scenarios as flowcharts, or DFDs, and not give up. Even when you feel it.

But…
The vulnerability discovery process can be something that can make you feel “How did this happen?!” You will find some vulnerabilities straightforward to discover (e.g. search for “exec” and follow code execution flow). But this is not the case for others, especially when the application contains a large code base. You would also think, as to how did we reach here? And that cannot come to you that easy. A good friend of mine said: “Some foresight is required, and foresight requires experience. There’s no shortcut to ‘teach’ vulnerability discovery because it can be extremely subtle; do more code review to get better at vulnerability discovery.”
Enter the Dragon: OSWE Certification Attempt
Some general tips for the certification attempt:
- OSCP is a 24 hours exam, while OSWE is a 48 hours exam. You do not have to run fast in this exam unlike OSCP. OSCP is a sprint. This is a marathon. Take breaks, eat, sleep – refresh yourself as much as possible.
- Make sure you are familiar with the debugging tools, since you would be extensively engaging with them mostly, such as Notepad++ searching capabilities, dnSpy, regex101.com, JD-GUI.
- While going through the course, you would come across some more challenging than usual exercises, which OffSec refers as ‘Extra Miles’. These exercises do not guarantee passing the exam, but they allow one to think out of the box to solve certain problems. Some are very easy (can be solved in 5 minutes), while some are seemingly frustrating (can take up to 2 weeks, and depends how much time you invest in researching, viewing relevant videos, blogs, etc.).
- Enjoy :-)
Bonus
- When you start off with your labs, go to Netsec Focus. The place will help you to share your problems in an abstract manner to give you relevant hints that’ll help you get absolute results. Also, you can interact with different students who have enrolled into the course to exchange ideas. The best part is that ronin and ryujin are also part of that platform and you can ask for some assistance in case you feel stuck somewhere.
- There are ways to reach to the end goal while dealing with problems in exercise / extra miles section. Be curious and follow the code flow.
- Make sure you have weekends to spare for trying harder, unless of course you find the information in contents page pretty easy.
- Friday the 13th: JSON attacks – An interesting, as well as relevant video one should watch.
- OWASP Code Review Guide v1.1 is an excellent document if you want to achieve a basic understanding of secure code review practice.
Summary
This course was really challenging and engaging at the same time. It is probably one of the best courses that make you accustomed to source code review practices and pushes one’s limits for hunting security issues residing in source codes of web applications. I really thank Offensive Security for making this course available for all.
Free Download: Web Application Security guide
